Q1 2025 Data Breach Report: 658 Data Breaches Reported and Major Database Improvements
Posted: May 23 2025
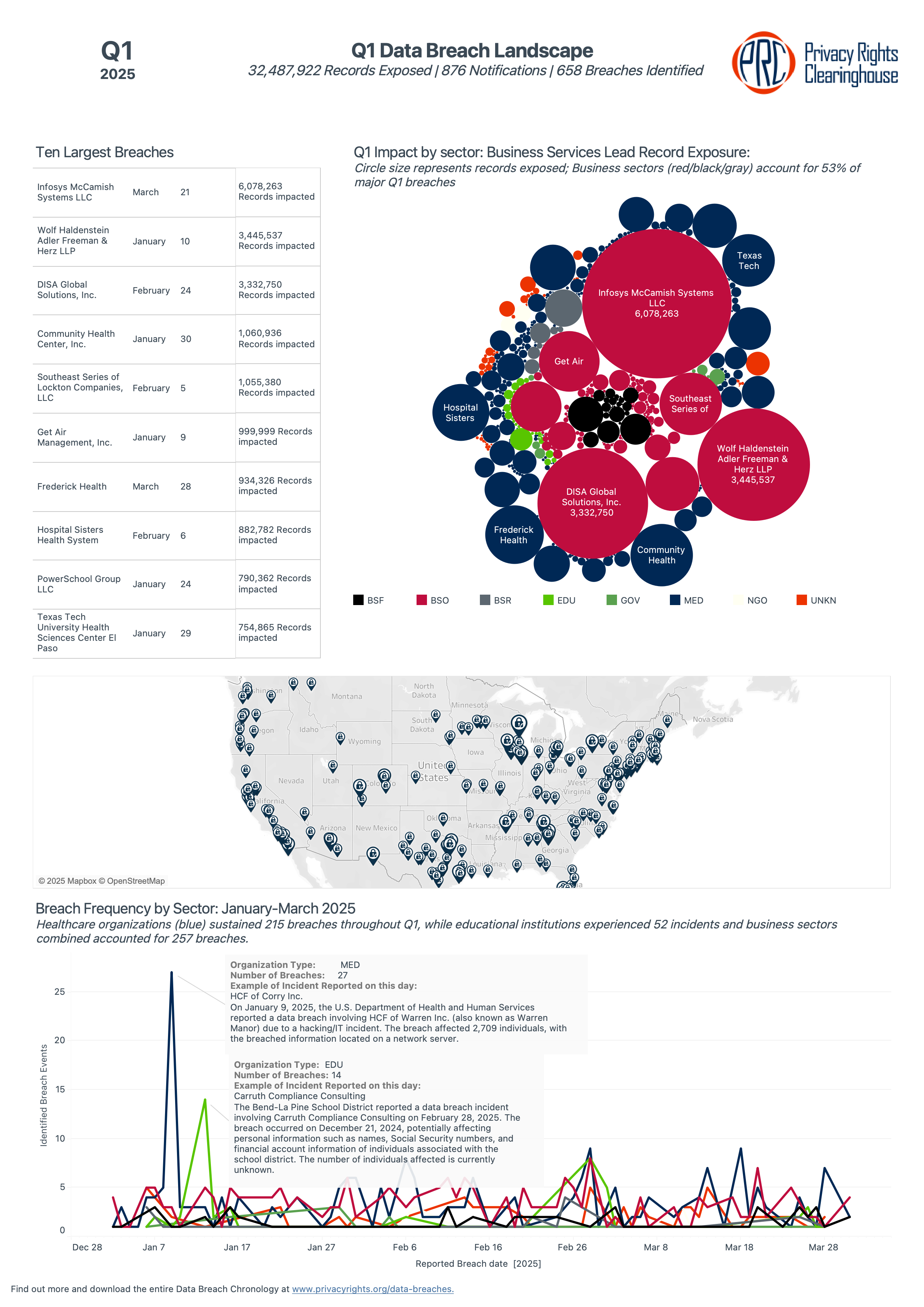
Our May 2025 update—the fifth this year—brings our complete data through May along with this focused analysis of Q1 breach statistics. The first quarter saw 876 new breach notifications representing 658 distinct security incidents that impacted over 32 million people. This release also includes major database enhancements with completely refactored grouping algorithms and improved categorization models, making our breach tracking and analysis more accurate than ever.
While healthcare organizations continued to face significant breach activity and hacking remained the dominant attack method, the combined business sectors actually experienced the most incidents overall. The quarter saw several massive breaches, including Blue Shield of California's 4.7 million-record incident, while ongoing notifications from breaches dating back to 2023 remind us that breach impacts extend well beyond initial disclosure dates.
Check out our infographic below and share widely, and read on for more information on the 2025 Q1 data breach landscape.
Q1 2025 By the Numbers
From January through March 2025, we recorded:
- 876 new breach notifications
- 658 distinct breach incidents (561 newly reported + 97 with ongoing activity)
- 32,487,922 people potentially impacted
Four major new breaches affecting over 1 million people each were first reported this quarter:
- Blue Shield of California: 4.7 million records
- DISA Global Solutions: 3.3 million records
- Community Health Center, Inc.: 1.06 million records
- Southeast Series of Lockton Companies: 1.03 million records
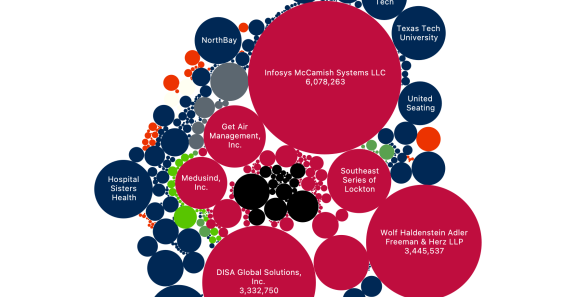
Additionally, ongoing notification activity from previously reported breaches included significant incidents like Infosys McCamish Systems (originally from 2023) affecting over 6 million people and Ascension Health impacting 5.6 million.
Breach Types and Patterns
Hacking incidents continued to dominate the breach landscape, accounting for 400 of the 658 total incidents (61%). The remaining incidents were largely categorized as unknown breach types (249 incidents, 38%)—cases where notification documents don't provide sufficient detail to determine the specific attack method—along with smaller numbers of disclosure incidents (28) and other breach types.
Healthcare organizations bore the heaviest burden with 215 incidents (33% of the total), followed by business services organizations with 184 incidents (28%). When combined, all business sectors—including business services, financial services, and retail—accounted for 257 incidents or 39% of the quarter's total, making the broader business community the most affected sector overall. The healthcare sector also saw some of the largest individual breaches, including the Blue Shield of California's incident we mentioned earlier, affecting 4.7 million people and Community Health Center's breach impacting over 1 million people.
An important aspect of Q1's activity involved ongoing breaches from previous periods. While 561 incidents were newly reported, 97 represented continued notification activity from breaches originally discovered in earlier months or years. Some of these ongoing incidents had massive scope, including Infosys McCamish Systems (originally from 2023) affecting over 6 million people and Ascension Health impacting 5.6 million people.
Database Improvements and What's Next
This quarter's release includes some major behind-the-scenes improvements. We've completely rebuilt how we group related breach notifications. Since a single breach can generate dozens of separate state filings, our new grouping algorithms better identify when multiple notifications refer to the same incident. This gives everyone more accurate breach counts.
We've also rerun all our categorizations with improved models. This means better classification of breach types, organization types, and the kinds of information exposed. We're slowly reducing those "unknown" categories wherever possible. Many of these improvements came directly from feedback we've received from researchers, journalists, and advocates who use the database.
As always, we'll continue our monthly updates with the latest breach notifications as they come in. If you're using the database for research or reporting and have suggestions for improvements, we'd love to hear from you. The more people dig into this data, the better we can all understand and hopefully prevent future breaches.
Explore the Data
Visit the Data Breach Chronology to explore the full database and contribute to the broader conversation about improving data protection and security practices.